Authentication
Private Applications (API Key)
Private applications are designed for use cases where you are connecting to your own ServiceM8 account, or to one specific customer's account, and do not intend to promote/list your add-on on the ServiceM8 Add-ons Directory or promote it to a wider audience.
ServiceM8 uses API keys to authenticate integration requests. You or your developer will generate this key from your ServiceM8 account to establish a secure connection.
You do not need a ServiceM8 Developer account to use API keys
To create an API Key, go to Settings -> API Keys
Using Your API Key
Once you have generated your API key, you must include it in all API requests by setting it in the X-API-Key header.
Example Request
curl -X GET "https://api.servicem8.com/api_1.0/company.json" \
-H "X-API-Key: your_api_key_here"
-H "Content-Type: application/json"Getting Started with a Private Application
- Private applications can connect directly to the ServiceM8 API using your ServiceM8 API Key.
- Read up on the REST API for information on how to access and update your data
Public Applications (OAuth 2.0)
Public applications are designed for external apps or add-ons targeted at all ServiceM8 users. Public applications have additional benefits over private applications such as:
- Potential to be listed in the ServiceM8 Add-ons Directory
- Can send SMS and Email messages via the ServiceM8 Platform
- Web-hooks provide real-time data updates
- Seamless integration with the ServiceM8 Platform UI – including preferences, custom fields, badges and other functionality
Getting Started with a Public Application
- Register as a Development Partner
- Login to your account, then click the Developer link in the main menu
- Click “Add Item” to create your add-on
- After you save your add-on, you’ll be issued with an App Id and App Secret
- Implement OAuth 2.0 Authentication in order to allow your add-on to access customer’s ServiceM8 accounts
Signing up as a Development Partner, creating a Public Application, and implementing OAuth 2.0 is required in order to take advantage of some ServiceM8 APIs. This does not mean you have to make your add-on publicly available. You can create a Public Application and choose not to list it on the ServiceM8 Add-on Store.
Implementing OAuth 2.0
If you are already familiar with OAuth 2.0, the information you'll need to know is listed here:
| Authorize URL | <https://go.servicem8.com/oauth/authorize> |
| Access Token URL | <https://go.servicem8.com/oauth/access_token> |
| Supported grant types | authorization_code, refresh_token |
| Access Token Lifetime | 3600 seconds |
| Supported Scopes | Refer to table at the bottom of this page. |
If you haven't implemented OAuth 2.0 before, read on for more detailed guidance.
Every app is issued an App ID and App Secret. These are shown on your app’s Store Connect page inside your partner account. Your App ID uniquely identifies your app to ServiceM8, and your App Secret serves a similar purpose to a password, allowing your app to prove its identity when required.
Keep it secret, keep it safeYour App Secret (as its name suggests) must be kept secret. If a third party gets access to it, they’ll be able to impersonate your app and get access to any ServiceM8 account that your app is connected with.
There are several steps that an app must complete in sequence to authenticate against an account. At the end of the authentication process, a token is generated that allows the app to make calls to the API on behalf of an account.
Initiating Authentication
To initiate authentication, redirect the user to the following URL:
https://go.servicem8.com/oauth/authorizewith the following parameters encoded in the query string:
| Parameter | Description | |
|---|---|---|
| response_type | required | OAuth type. Use “code” when requesting a new access token |
| client_id | required | The App ID of your app |
| scope | required | The list of required scopes (explained below). If requesting multiple scopes, separate them with a space. |
| redirect_uri | optional | The URL that the user will be sent to once authentication is complete. This URL must be the same host as the Return URL specified in the Store Connect settings. |
For example, if your App ID is 0314159, you would like to request the read_customers and read_jobs scopes, and your OAuth redirect url is https://myapp.example.com/HandleOAuth, then send your user to the following URL:
https://go.servicem8.com/oauth/authorize?response_type=code&client_id=0314159&scope=read_customers%20read_jobs&redirect_uri=https%3A%2F%2Fmyapp.example.com%2FHandleOAuth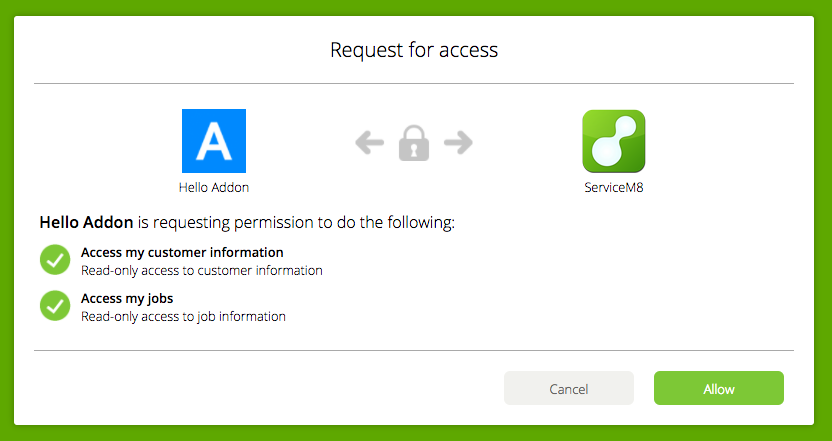
Once here, the user will be asked to grant the requested permissions.
Assuming that the user grants access, ServiceM8 redirects them to the redirect_uri specified by the app with a temporary access token code as a parameter. Given the redirect URL https://myapp.example.com/HandleOAuth the call will look like this: GET https://myapp.example.com/HandleOAuth?code=TEMP_TOKEN
Exchanging the Temporary Token
Exchange the temporary token for a permanent access token by making a HTTP POST request to the token endpoint:
https://go.servicem8.com/oauth/access_tokenwith the following POST parameters:
| Parameter | Description | |
|---|---|---|
| grant_type | required | OAuth grant type. Use "authorization_code" |
| client_id | required | The App ID for your app. |
| client_secret | required | The App Secret for your app. |
| code | required | The temporary token you received in the prior step. |
| redirect_uri | required | Must be identical to the redirect URI provided previously |
The response will contain your Access Token as well as a Refresh Token.
{
"access_token": "your_access_token_here",
"expires_in": 3600,
"token_type": "bearer",
"scope": "read_customers read_jobs",
"refresh_token": "your_refresh_token_here"
}Using the Access Token
Use the token to access the API. To do this, include the variable access_token as a POST parameter on all requests to the API, or supply the access token, prefixed with "Bearer " on the HTTP "Authorization" header. Access Tokens have a limited lifespan (currently one hour). To continue accessing the account after the token has expired, you need to obtain a new Access Token using the Refresh Token.
Using the Refresh Token
To obtain a new Access Token, make a HTTP POST request to the token endpoint
https://go.servicem8.com/oauth/access_tokenwith the following POST parameters
| grant_type | required | OAuth grant type. Use "refresh_token" |
| client_id | required | The App ID for your app. |
| client_secret | required | The App Secret for your app. |
| refresh_token | required | The Refresh Token provided when you obtained the Access Token. |
The response will contain your Access Token as well as a new Refresh Token.
{
"access_token": "your_new_access_token_here",
"expires_in": 3600,
"token_type": "bearer",
"scope": "read_customers read_jobs",
"refresh_token": "your_new_refresh_token_here"
}Scopes
Scopes are strings that enable access to particular resources, such as user data. You include a scope in certain authorization requests, which then displays appropriate permissions text in a consent dialog that is presented to a user. Once the user consents to the permissions, ServiceM8 sends your app tokens, which identify the specific authorisation grant. In other words, the scopes and tokens determine what user data the user gives your app permission to access.
ServiceM8 supports incremental authorisation. This feature enables your app to request initial permissions at sign-in and additional permissions at a later time, typically just before they are needed. For example, if your app allows users to create jobs, you can ask for basic user information at sign-in, and later ask just for job creation permissions when the user is ready to create their first job. At this point, the consent dialog box asks the user only for the new permissions, which gives them a simpler, in-context decision to make. You might use this technique if you suspect users are not signing in because your consent screen is overwhelming, or are confused as to why they are being asked for certain permissions. This feature can improve your sign-in conversion rate if you configure your initial scopes to be only the minimum that your app requires to get the user started.
The following scopes, with user consent, provide access to otherwise restricted user data.
To get more, only scope what you needLimit your API scopes to the essentials and unlock a higher rate limit as your reward. Eg. don't just add every scope.
| Scope | Description |
|---|---|
| staff_locations | Access to real-time GPS information about staff |
| staff_activity | Access to clock on, lunch break and clock off information about staff |
| publish_sms | Access to send SMS messages to customers and/or staff on your behalf. Note: sending SMS messages will incur account charges. |
| publish_email | Access to send Email messages to customers and/or staff on your behalf |
| vendor | Access to basic account information |
| vendor_logo | Access to account logo |
| vendor_email | Access to account holder email address |
| read_locations | Read-only access to Location Endpoint |
| manage_locations | Full access to Location Endpoint |
| read_staff | Read-only access to Staff Endpoint |
| manage_staff | Full access to Staff Endpoint |
| read_customers | Read-only access to Company Endpoint |
| manage_customers | Full access to Company Endpoint |
| read_customer_contacts | Read-only access to CompanyContact Endpoint |
| manage_customer_contacts | Full access to CompanyContact Endpoint |
| read_feedback | Read-only access to the Feedback Endpoint |
| manage_feedback | Full access to the Feedback Endpoint |
| read_jobs | Read-only access to Job Endpoint |
| manage_jobs | Full access to Job Endpoint |
| create_jobs | Ability to create jobs on behalf of account. Note: creating jobs may incur account charges. |
| read_job_payments | Read-only access to JobPayment Endpoint |
| manage_job_payments | Full access to JobPayment Endpoint |
| read_job_contacts | Read-only access to JobContact Endpoint |
| manage_job_contacts | Full access to JobContact Endpoint |
| read_job_materials | Read-only access to JobMaterials Endpoint |
| manage_job_materials | Full access to JobMaterials Endpoint |
| read_job_categories | Read-only access to Categories Endpoint |
| manage_job_categories | Full access to Categories Endpoint |
| read_job_checklists | Read-only access to Job Checklists Endpoint |
| manage_job_checklists | Full access to Job Checklists Endpoint |
| read_job_queues | Read-only access to Job Queues Endpoint |
| manage_job_queues | Full access to Job Queues Endpoint |
| read_tasks | Read-only access to Tasks Endpoint |
| manage_tasks | Full access to Tasks Endpoint |
| read_schedule | Read-only access to JobActivity and JobAllocation Endpoints |
| manage_schedule | Full access to JobActivity and JobAllocation Endpoints |
| read_security_roles | Read-only access to SecurityRole Endpoint |
| read_inventory | Read-only access to Materials and MaterialBundles Endpoint |
| manage_inventory | Full access to Materials and MaterialBundles Endpoint |
| read_job_notes | Read-only access to job notes |
| publish_job_notes | Ability to add new job notes |
| read_job_photos | Read-only access to job photos |
| publish_job_photos | Ability to add new job photos |
| read_job_attachments | Read-only access to existing job attachments, quotes and invoices |
| publish_job_attachments | Ability to add new file attachments to jobs |
| read_inbox | Read-only access to inbox messages |
| read_messages | Read-only access to staff messages |
| manage_notifications | Ability to read notifications and mark as read |
| manage_templates | Full access to email, sms and document templates |
| manage_badges | Full access to create/modify job badges |
| read_assets | Read-only access to Assets, AssetType and AssetTypeField endpoints |
| manage_assets | Full access to Asset, AssetType and AssetTypeField endpoints |
| read_forms | Read-only access to Forms, FormResponse endpoints |
| manage_forms | Full access to Forms, FormResponse endpoints |
| read_tax_rates | Read-only access to TaxRate endpoint |
| manage_tax_rates | Full access to TaxRate endpoint |
User Impersonation
By default your app will receive the full privileges you have been granted by the user. For some requests it is desirable to POST data as a given account user rather than as your app itself. Eg. If you are a staff messaging app, you would post messages to other staff on behalf of the current user authenticated with your app. User impersonation automatically implements security for a given user, for example querying the jobs endpoint for all jobs as a restricted staff member will result in only records being returned that specific staff member is authorised to view.
To impersonate an account user, you must set the header “x-impersonate-uuid” in your API GET/POST/PUT/DELETE request. ‘x-impersonate-uuid’ must be an active, valid staff uuid for the current account.
Connecting your App from the ServiceM8 Add-on Store
If your app is installed from the ServiceM8 Add-on Store then the user will be redirected to your default app URL as defined in the app’s store connect settings. You will then have to start the auth process as described above.
Revoking access to a token or application
At any time, a user can revoke access to any connected application by disabling the Add-on from within the ServiceM8 Add-on Store.
Updated 7 months ago
